Are you interested in the world of cryptography but don’t know where to start? Look no further! This beginner’s guide will give you a solid foundation of knowledge to help you understand the basics of cryptography.
Cryptography has been around for thousands of years and has played a crucial role in protecting sensitive information. From ancient Greeks using secret codes to transmit messages during wartime to modern-day encryption algorithms used to secure online banking transactions, cryptography has come a long way.
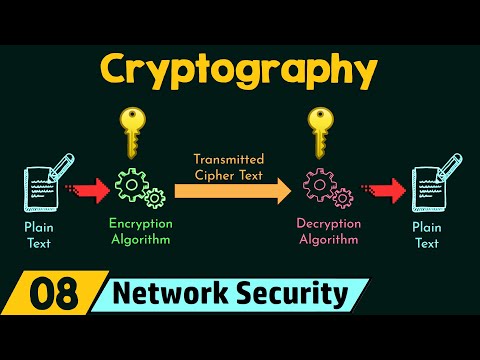
Reference: "Cryptography" by Neso Academy
Understanding the history and evolution of cryptography is essential to understand the importance of cryptography in today’s digital age. Let’s dive in and explore the world of cryptography together!
Table of Contents
History of Cryptography
The historical account of cryptography provides valuable insights into the evolution of secure communication methods. Over time, the techniques used in cryptography have evolved, from simple substitution ciphers to complex algorithms.
Some of the most famous historical uses of cryptography include the Caesar cipher used by Julius Caesar to send secret messages to his generals, and the Enigma machine used by the Germans during World War II.
As technology has advanced, so too has the field of cryptography, with new methods being developed to secure data in the digital age. Understanding the history of cryptography is essential in understanding the importance of secure communication and the ongoing effort to protect sensitive information.
Basics of Encryption and Decryption
So, you want to know about the basics of encryption and decryption. Well, let’s start with the two main types of encryption: symmetric and asymmetric.
Symmetric encryption uses the same key for both encrypting and decrypting data, while asymmetric encryption uses a pair of public and private keys.
Another important aspect is key management, which involves securely storing and sharing keys to ensure the security of encrypted data.
Symmetric and Asymmetric Encryption
You’re going to love learning about the different types of encryption, it’ll blow your mind!
There are two main types of encryption: symmetric and asymmetric. Symmetric encryption, also known as shared secret encryption, uses the same key for both encryption and decryption. It is further divided into two types: stream cipher and block cipher.
In stream cipher, the message is encrypted one bit at a time, while in block cipher, the message is divided into blocks of fixed size and then encrypted.
Asymmetric encryption, also known as public key encryption, uses different keys for encryption and decryption. The public key is used for encryption, while the private key is used for decryption.
Asymmetric encryption is more secure than symmetric encryption but is slower and requires more computing power.
Key Management
You’ll need to master the art of key management if you want to ensure the security of your sensitive data and prevent unauthorized access.
Key management involves two important processes: key generation techniques and key distribution methods. Key generation techniques are used to create unique and strong keys that are needed for encrypting and decrypting data. These techniques include random number generation, hash functions, and key derivation functions.
Once the keys are generated, the next step is to distribute them securely to the intended recipients. This is where key distribution methods come into play, which include symmetric key distribution, asymmetric key distribution, and key agreement protocols.
It’s important to choose the right key generation and distribution methods based on the specific security requirements of your system. Proper key management can help you maintain the confidentiality, integrity, and availability of your data.
Types of Cryptographic Algorithms
As you dive into the different types of cryptographic algorithms, you’ll soon realize that they are like puzzle pieces that fit together to create a complex shield of protection for your data.
There are two main categories of cryptographic algorithms: stream ciphers and block ciphers. Stream ciphers encrypt data one bit or byte at a time, whereas block ciphers encrypt data in fixed-size blocks.
Within these categories, there are various algorithms such as the Advanced Encryption Standard (AES) or the Data Encryption Standard (DES).
Additionally, hashing algorithms are used for data integrity, ensuring that the data hasn’t been tampered with. Examples of hashing algorithms include SHA-256 and MD5.
Understanding these types of cryptographic algorithms and how they work together is essential for safeguarding your data.
Importance of Digital Certificates and Public Key Infrastructure
To ensure the security of your digital transactions, it’s crucial to understand the importance of digital certificates and how they work within the public key infrastructure.
Digital certificates are used to verify the identity of a user or device in a network. They contain information such as the owner’s name, public key, validity period, and the certificate authority that issued it.
Digital certificates play a vital role in establishing trust between parties by ensuring that the information being exchanged is legitimate and not tampered with.
However, implementing public key infrastructure can be challenging, as it requires a reliable and secure system to manage certificates, revoke them when necessary, and ensure their validity.
Nevertheless, the benefits of using digital certificates and public key infrastructure far outweigh the challenges, as they provide a secure and efficient way to protect your sensitive information online.
Frequently Asked Questions
How long does it take to crack a modern encryption algorithm?
If you’re wondering how long it takes to crack a modern encryption algorithm, the answer is that it depends on a few factors.
Average timeframes can vary depending on the strength of the encryption used, the length of the key, and the computing power of the attacker.
The most straightforward method of cracking encryption is brute force, which involves trying every possible combination of characters until the correct one is found.
With modern encryption algorithms, however, this method can take an incredibly long time, often years or even centuries, making it impractical for most attackers.
Can quantum computers break encryption algorithms?
Hey, you might want to sit down for this one. Did you know that quantum computers have the potential to break modern encryption algorithms in minutes? Yes, you read that right. It’s not just a possibility, it’s a reality.
However, don’t panic just yet. There’s a solution to this problem – post quantum cryptography. This type of cryptography is designed to be quantum-resistant, meaning that even with the power of a quantum computer, it would take millions of years to break the encryption.
So, while the threat of quantum computers breaking encryption algorithms is real, the solution is already in the works. Stay safe and keep your data secure with the help of post quantum cryptography.
How do hackers use cryptography to carry out cyber attacks?
You may be surprised to learn that hackers use cryptography to carry out cyber attacks. In fact, they often use it to gain access to sensitive information that is encrypted, such as passwords or credit card numbers.
Cryptography in social media and online banking is especially important because it protects your personal data from being intercepted by hackers. However, hackers can also use cryptography to hide their own malicious activities, making it difficult for authorities to trace them.
It’s important to understand the basics of cryptography and how it is used in different contexts to ensure that your information is as secure as possible.
What is the relationship between cryptography and blockchain technology?
If you’re interested in the relationship between cryptography and blockchain technology, you might be curious about the integration possibilities.
Blockchain technology uses cryptography to secure and verify transactions, making it a natural fit for the use of cryptography in supply chain management.
Ensuring data integrity is key in supply chain management, and cryptography can help achieve that by providing secure communication channels and protecting sensitive information.
By combining these two innovative technologies, businesses can create a more secure and transparent supply chain system.
How do governments regulate the use of cryptography in different countries?
Are you curious about how governments around the world regulate the use of cryptography? Well, it’s a complex topic with a global impact.
The level of regulation varies from country to country, with some countries placing strict restrictions on the use of cryptography while others take a more liberal approach.
These regulations can have significant industry implications, particularly for companies that rely on cryptography for their business operations.
As technology continues to advance, it’s likely that cryptography regulation will continue to evolve, making it important for businesses to stay up-to-date with the latest developments in this area.
Conclusion
Well done, you’ve made it to the end of this beginner’s guide to cryptography! As you now know, cryptography has been around for centuries, even dating back to ancient civilizations. It has evolved over time to become an essential tool in modern-day communication, finance, and security.
Now that you understand the basics of encryption and decryption, as well as the different types of cryptographic algorithms, you can appreciate how important it is to keep our data secure. And let’s be honest, with the increasing reliance on technology in our daily lives, we could all benefit from a little more security.
So, the next time you use online banking or send a private message, take a moment to thank cryptography for keeping your information safe.
But hey, who needs privacy and security anyway? Let’s just put all our personal information out there for the world to see. After all, who doesn’t love a good data breach?
In all seriousness, though, it’s crucial to understand the importance of cryptography and to take steps to protect our sensitive information. So, keep learning, keep encrypting, and keep your data safe.


